Reverse Engineering Sig21CTF IIUM
Reverse Engineering Sig21CTF IIUM
Flag 1.
We were given a binary file to download named cr4ckm3001 simply running strings on the file then search for the flag format will us the flag
1
2
3
strings cr4ckm3001 | grep "sig21CTF{.*}"
sig21CTF{5c006c88c9e49482e94e4232b0c5a90a8217648d3d3fc90c8ff73b40150716d3}
Flag 2.
Ok this challenge is a little bit hard. running strings doest give us the flag. So its about time to use some real RE tools (as the challenge suggested). So for this challenge i will be using radare(r2).
1
2
3
r2 cr4ckm3002
aaaa -> to analize the binary
vb -> to print functions
Inspecting the entro of the program aka main() should give us the flag.
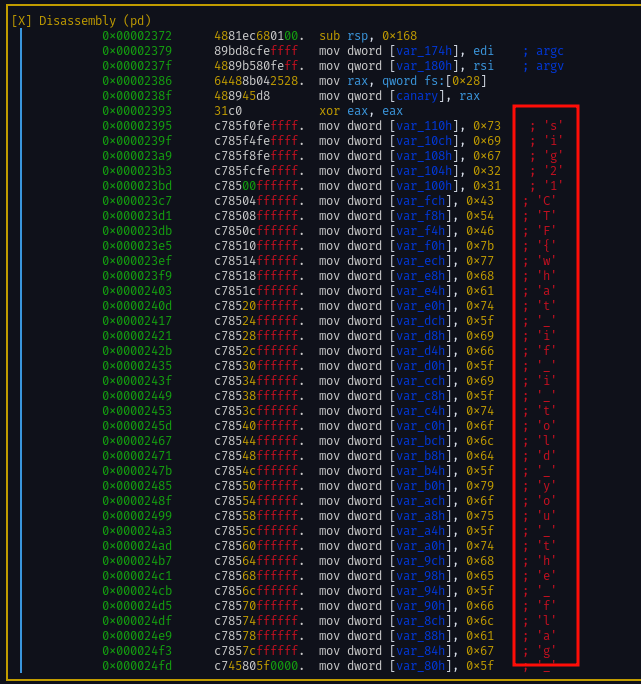
Flag 3.
Opening the main in r2 we can see the assembly code.
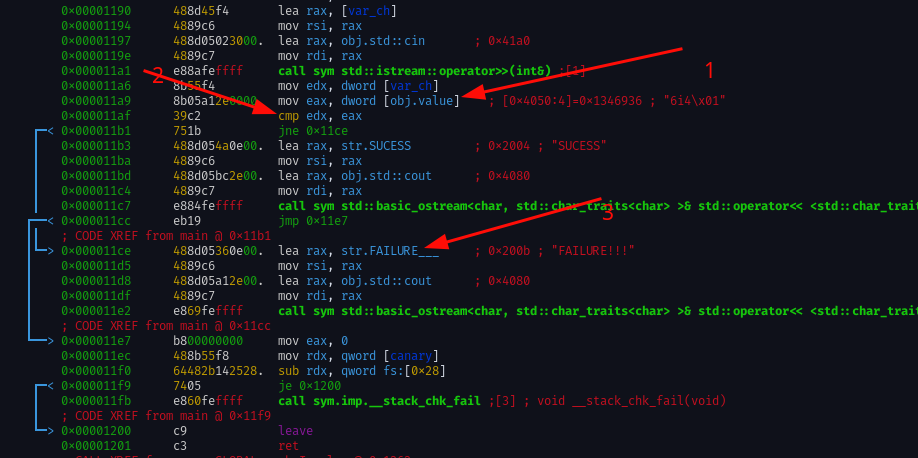
Step 1.
We move $dword to $aex $aex = 0x1346936
0x1346936 to decimal == 20212022
Step 2.
we compare if $edx == $aex
1
2
if (input == 202122) {print success}
else {print failure}
then we jne (jump not equal) to the failure mesage. So theoritically if we supply 20212022 we should get a success msg.
Step 3.
We print Failure
Flag
1
2
3
echo "20212022" | md5sum
dca92a085ebc8a1a668c08a4954e1dd0
flag: sig21CTF{dca92a085ebc8a1a668c08a4954e1dd0}
Thanks for reading, I hope this helps :)
This post is licensed under CC BY 4.0 by the author.